Introduction to Zoho data security
Data security is paramount in our current digital landscape, for both companies and individuals. Growing cyber threats have led to heightened user anxieties regarding the protection of their personal and business data within cloud platforms. Zoho, a well-known global SaaS vendor offering a range of business applications, is one such platform that frequently prompts inquiries about its security.
Therefore, this blog post will delve into Zoho’s security protocols, its adherence to international regulations, and the methods it employs to safeguard your confidential data, addressing the question of how secure your data truly is when using Zoho.
Understanding Zoho’s Commitment to Security
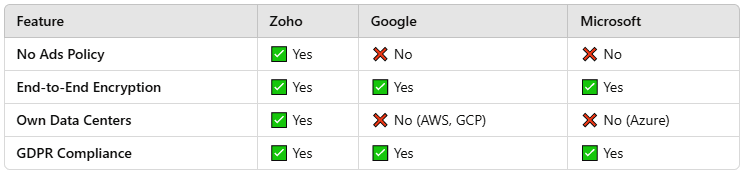
Zoho places a high value on privacy, transparency, and security, guaranteeing the protection of customer data. In contrast to many large technology companies that depend on advertising revenue, Zoho adheres to a firm no-advertising and no-tracking policy, ensuring that user data is never sold to external entities.
Zoho uses its own data centers, giving them full control over security and minimizing reliance on external cloud services. Zoho’s reliance on its own data centers, rather than third-party cloud providers, ensures total command over its security protocols.
Encryption and Data Protection
End-to-End Encryption (E2EE)
End-to-End Encryption (E2EE) guarantees user data is encrypted while being transmitted and while stored. With End-to-End Encryption (E2EE), user data remains encrypted whether it’s being sent or stored. End-to-End Encryption (E2EE) protects user data by encrypting it during both transmission and storage. E2EE ensures data security by encrypting user information from the sender to the recipient and while stored.
AES-256 Encryption
AES-256 encryption provides maximum data protection, employing a military-grade standard. For maximum data protection, AES-256 encryption, a military-grade standard, is utilized. Data is protected at the highest level using AES-256 encryption, a standard often described as military-grade. AES-256 is a military-grade encryption standard designed to ensure maximum data protection.
SSL/TLS Protocols
To protect data from hackers, Zoho encrypts all data transferred between users and its servers using SSL/TLS protocols. Using SSL/TLS protocols, Zoho encrypts all data in transit between users and its servers, ensuring protection against hackers. Zoho uses SSL/TLS protocols to encrypt all data transmitted between its servers and users, thereby preventing hackers from intercepting the information.
Compliance with Industry Standards
Zoho adheres to globally recognized security frameworks and complies with various data protection regulations, including:
GDPR (General Data Protection Regulation)
The General Data Protection Regulation (GDPR) protects the data privacy and rights of users within the European Union. GDPR, or the General Data Protection Regulation, guarantees data privacy and safeguards user rights for customers in the EU. To protect EU customer data privacy and user rights, our company adheres to the General Data Protection Regulation (GDPR).
ISO 27001 & 27017
ISO 27001 and ISO 27017 are recognized as industry-leading certifications for information security management. For robust information security management, the industry relies on certifications like ISO 27001 and ISO 27017. Attain industry-leading information security management with ISO 27001 and 27017 certifications. ISO 27001 and 27017 represent the gold standard in certifications for information security management. Demonstrate excellence in information security management by achieving ISO 27001 and ISO 27017 certifications.
SOC 2 Type II Compliance
SOC 2 Type II compliance confirms Zoho’s capability to safeguard data against unauthorized access. Zoho’s SOC 2 Type II compliance demonstrates their effectiveness in protecting data from unauthorized access. Achieving SOC 2 Type II compliance verifies Zoho’s system for securing data and preventing unauthorized access. Zoho has achieved SOC 2 Type II compliance, proving their ability to protect data against unauthorized access.
HIPAA Compliance
Ensuring HIPAA compliance for the protection of sensitive healthcare data within Zoho applications.Zoho applications and HIPAA compliance: Safeguarding sensitive healthcare data. Achieving HIPAA compliance: Protecting healthcare information using Zoho applications.
Comparing Zoho’s Security with Competitors
Conclusion
Businesses worldwide trust Zoho because of its strong, privacy-centric ecosystem, built with user security as a priority. Advanced encryption, global regulatory compliance, secure infrastructure, and proactive threat management underpin Zoho’s commitment. Zoho’s ecosystem prioritizes user privacy and security through advanced encryption, adherence to global regulations, a secure infrastructure, and proactive threat management, making it a robust and trusted solution for businesses.
Zoho’s dedication to user security is evident in its robust, privacy-focused ecosystem, which utilizes advanced encryption, complies with global regulations, maintains a secure infrastructure, and proactively manages threats, ensuring a trustworthy experience for businesses around the world.
Frequently Asked Questions (FAQs) on Zoho Data Security
1. Is Zoho secure for enterprise use?
Yes, Zoho is highly secure for enterprises. It complies with GDPR, ISO 27001, SOC 2 Type II, and HIPAA standards, ensuring data protection at every level. Additionally, Zoho uses end-to-end encryption, secure authentication, and regular security audits to safeguard enterprise data.
2. Does Zoho sell or share user data with third parties?
No, Zoho follows a strict no-ad, no-tracking policy. Unlike many other SaaS providers, Zoho does not sell or share user data for advertising or marketing purposes. Your data remains private and fully owned by you.
3. What measures does Zoho take to prevent cyber threats?
Zoho employs 24/7 security monitoring, DDoS protection, advanced firewalls, AI-driven threat detection, and regular vulnerability assessments to prevent cyberattacks. It also follows a Zero Trust Security Model to verify every access request before granting permissions.
4. How can I enhance the security of my Zoho account?
To maximize security, follow these best practices:
✅ Enable Two-Factor Authentication (2FA) for an extra layer of security.
✅ Use strong, unique passwords and update them regularly.
✅ Restrict access with Role-Based Access Control (RBAC) for employees.
✅ Monitor account activity and report suspicious logins immediately.
5. What happens if Zoho experiences a data breach?
Zoho has a robust disaster recovery and incident response plan in place. In case of a breach, Zoho will:
- Immediately notify affected users as per compliance regulations.
- Secure and recover compromised data using automated backup systems.
- Conduct a thorough investigation and implement stronger safeguards to prevent future incidents.
Ready to Take Your Business to the Next Level?
If you need help setting up custom apps with ZOHO or want expert guidance, get in touch with us today!
For more info related to ZOHO read this.
📞 Phone: +91 7838402682
📧 Email: team@codroiditlabs.com
🌐 Website: www.codroiditlabs.com
